Security is one of the important factors that every developer considers during web application development. If your application is not secure, then it will result in losing your user’s trust and they’ll move away.
Never miss an update from us. Join 10,000+ marketers and leaders.
In this article, we will mainly focus on the ruby on rails guide to “ secure your Rails application”. Therefore here you can see some important steps that you can follow for your ruby on rails security.
What Is Session?
In networking “Session” indicates the time of browsing a website by a user, a semi-permanent information exchange between a user and a computer. In a session, the user has to authenticate on every request for his identity. As Webpages are having no memories, sessions are helpful for users to be recognized within a website/application.
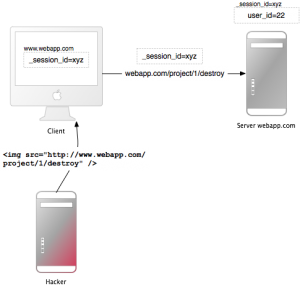 (Source: rubyonrails.org)
(Source: rubyonrails.org)
Rails create a new session when a new user accesses the application and loads the existing session if the user has already used the same. In the Rails app a session usually consists of a hash of values and a session id. The session id is a 32-character string; it helps to identify the hash. It is possible to save and retrieve the values using the session method.
To set data:
def create
# …
session[:current_user_id] = @user.id
# …
end
To retrieve the data:
def index
current_user = User.find_by_id(session[:current_user_id])
# …
end
There are several ways in which hackers use sessions to exploit sensitive information, such as Session Hijacking, Replay Attack, Session Fixation and Session Expiry.
It is the process of stealing a user’s session id so that the attacker can use the application in the user name. The session id in the cookie identifies the session. If someone sniffs the cookie in an insecure network may use the web application in the name of the user. It is prevented by providing a secure connection over SSL. In Rails 3.1 and later versions, it is done by forcing SSL connection in the “config. file”.
config.force_ssl = true
Replay Attacks For Cookie Store Sessions
A replay attack is a form of network attack in which valid data transmission is repeated or delayed maliciously using the CookieStore. To solve replay attacks include a nonce or random value in the sessions. Storing the nonce in a database table is the best solution. This will make the purpose of CookieStore entirely false.
Secure User Data:
New Rails developers get into the habits of displaying data using their ID. It has been a part of the ActiveRecord methods that is drilled into the young developers during the ruby on rails application development, they first learn to generate the RestFul Controllers by using CRUD actions. But by default this code doesn’t perform any kinds of authorization checks.
All the users of this application can see every record by changing the URL ID. To properly manage the roles and permissions, Rails has authorization to gems like CanCanCan or Pundit.
The simple way to make sure the user cannot access other’s data is by performing the query on the objects which belong to them (it also reduces the load of the query to speed up your rails application)
What Is Session Fixation?
When the attackers fix a user’s session id known to them, this is known as session fixation. They force the user’s browser to use the fixed id. Therefore, after this the attackers do not need to steal the sessions. It can be dangerous because the victim and the attacker will co-use the application, as the session is valid and the victim cannot even notice it.
To prevent Session Fixation, issue a new session identifier and make the previous one invalid after a successful login. This is how a new session is created in Rails:
reset_session

How To Expire A Session!
There are cases in which sessions never expires. This extends the period for attacks. It can be prevented by setting expiry time-stamp of the cookie with the session id.
Here is an example – how to expire a session in a database:
class Session < ActiveRecord::Base
def self.sweep(time = 1.hour)
if time.is_a?(String)
time = time.split.inject { |count, unit| count.to_i.send(unit) }
end
delete_all “updated_at < ‘#{time.ago.to_s(:db)}'”
end
end
The SSL is the only way to prevent sniffing attacks that are done with sessions. Large objects and critical data shouldn’t be stored in sessions. They should be stored in the database and save their id in session.
I’ve worked with the team at Andolasoft on multiple websites. They are professional, responsive, & easy to work with. I’ve had great experiences & would recommend their services to anyone.
Ruthie Miller, Sr. Mktg. Specialist
Salesforce, Houston, Texas
LEARN MORE
The SSL is the only way to prevent sniffing attacks that are done with sessions. Still there are some additional guidelines in Rails to secure the sessions. Large objects should not be stored in sessions. They should be stored in the database and save their id in session. In addition, critical data must not be saved in session. Many storage mechanisms are provided in Rails for session hashes, the most important of them is ActionDispacth::Session::CookieStore. Rails 2 also has introduced a default session storage called, “CookieStore”. This is helpful in preventing tampering.
Conclusion:
Worried!
Then start taking your Ruby on rails Security seriously. As it’s a part of your job whether you like it or not.
Despite implementing several security measures to your Ruby on Rails application, an experienced ROR developer is important, especially when implementing any solutions to the problems that contain any sensitive data.
@Andolasoft. We use Ruby on Rails as a core technology for delivering high quality secured web apps. We develop and maintain code base, use various technologies to protect you from hackers.
Do you have something to add up? Please drop in your comments below or talk to us.







