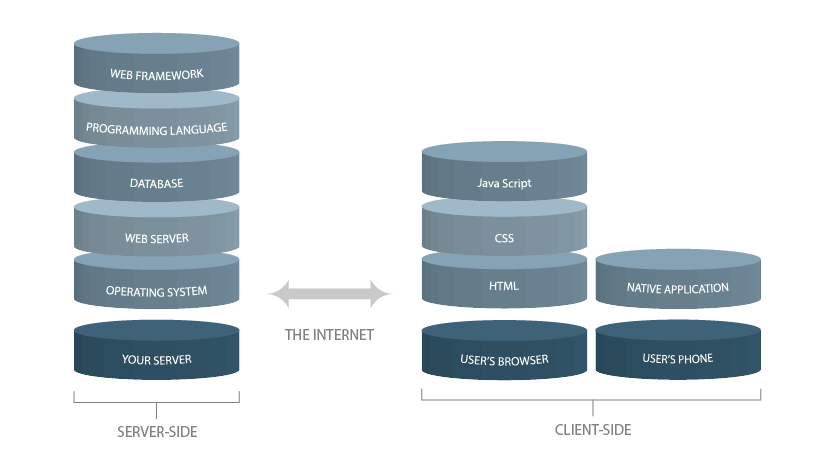
Cloud migration is a strategic business decision that enables organizations to move data, applications, and infrastructure to the cloud. This can unlock enhanced scalability, agility, and cost efficiency.
On the other hand, the process has many challenges. Organizations face pitfalls that can derail projects, leading to increased costs, operational disruptions, and security vulnerabilities.
In this blog, we will explore the top five most common cloud migration pitfalls and provide actionable strategies for avoiding them.
1. Inadequate Planning and Strategy
The Pitfall
One of the most significant mistakes organizations make is diving into cloud migration ventures without a pre-defined roadmap or strategies.
Rushing into it without thorough planning could result in misaligned goals, inefficient processes, and increased dependencies.
Without the right plan, you risk facing unexpected technical challenges, budget overruns, and operational inefficiencies.
Why It Happens
- Lack of Clear Objectives: Many businesses don’t have a clear objective about what they want with the migration such as cost reduction improved performance or enhanced security.
- Insufficient Stakeholder Involvement: When teams make decisions without taking inputs from business leaders the migration activities may not be productive for the business.
- Underestimating Complexity: Businesses often underestimate the complexity of migrating their legacy systems and application modernization activities.
How to Avoid It
- Develop a Comprehensive Migration Strategy: Start with a clear understanding of the business goals. Identify what you want from your migration venture. You should also consider developing a detailed framework including timelines, milestones, and responsibilities.
- Conduct a Thorough Assessment: Perform a comprehensive audit of your environment. Determine the dependencies, applications, data sets, and workflows that will be impacted. This audit process should determine the existing legacy systems as well as dependencies to avoid complications.
- Engage Stakeholders Early: Include all the team members and relevant stakeholders when deciding on the migration process. A cross-functional team can provide diverse perspectives which will ensure that your efforts align with the business strategies.
- Create a Detailed Roadmap: You can also break down the migration process into multiple phases. This will define the various checkpoints as well as lay out the various contingency plans to address the issues when they arise during the process.
By strategizing your efforts beforehand you can reduce the risk of unexpected hurdles.
2. Underestimating Data Complexity and Legacy Systems
The Pitfall
Project data is the single most valuable asset for any organization. Migrating it from a legacy system is a complex process and takes time.
Organizations oftentimes underestimate the complexities involved in transferring data accurately and securely.
These legacy systems can present compatibility issues which can complicate the migration process.
Why It Happens
- Data Silos and Disorganization: Oftentimes data remains scattered across multiple systems and formats, which makes it hard to integrate into modern cloud platforms.
- Legacy Application Dependencies: Many legacy systems rely on outdated technologies that don’t integrate effectively with cloud environments. This can lead to compatibility and performance issues.
- Volume and Velocity: Large data sets and the need for real-time access can affect migration efforts which can lead to data loss and corruption.
How to Avoid It
- Conduct a Data Audit: Determine the structure and volume of the data you want to migrate. Find the data silos as well as establish a data governance framework.
- Plan for Data Transformation: Not all data can be moved in its original format. You need to clean, transform, and reformat data to ensure that it’s compatible with the cloud platform.
- Leverage Automated Tools: Leverage migration tools and platforms when handling large data volumes; also minimize manual errors by automating data mapping processes.
- Test Extensively: Pre-migration testing will enable you to identify potential issues such as data compatibility and performance; which will in turn fine-tune your approach.
3. Overlooking Security and Compliance Requirements
The Pitfall
Security and compliance are necessary to adopt cloud solutions and need to be strategized beforehand. Yet, if you are overlooking these aspects your organizations will face significant risks.
When it comes to cloud environments, you need to configure them to prevent data breaches and avoid creating compliance violations and other cyber threats.
Why It Happens
- Assumption of Provider Responsibility: Some organizations believe that the cloud provider should exclusively take care of the application’s security. However, the cloud service providers provide robust security measures but the organization should themselves configure and manage security appropriately.
- Rapid Migration Pressure: Don’t skip security configurations and compliance checks to complete a migration
- Complex Regulatory Landscapes: Ensure to meet industry-specific regulations and standards such as GDPR, HIPAA, or PCI-DSS.
How to Avoid It
- Adopt a Security-First Approach: Integrate security considerations into every stage of your migration process. Develop a detailed security policy that covers data encryption, access controls, and incident response strategies.
- Understand Shared Responsibility: Define the right security responsibilities for your organization against those of the cloud providers. You need to configure all security settings such as firewalls, identity management, and monitoring tools.
- Ensure Regulatory Compliance: Team up with legal and compliance teams to map out all other regulatory needs that are relevant to the industry. Also, conduct regular audits and use compliance management tools to remain aligned with the regulations.
- Implement Continuous Monitoring: Once your data is in the cloud, it becomes imperative that you continuously monitor for vulnerabilities and unusual activity.
By addressing this security and compliance proactively, you can mitigate risks as well as ensure that your cloud environment is safe and compliant.
4. Mismanaging Costs and Budget Overruns
The Pitfall
Cost management is a significant factor when migrating to the cloud. If you have not planned out your budget, unexpected expenses can quickly add up.
Many organizations find themselves facing budget overruns due to hidden costs and unexpected operational expenses.
Why It Happens
- Underestimating Operational Costs: Many organizations focus on initial costs but don’t account for operational expenses. These expenses include data transfer fees, storage costs, and also cloud service management.
- Resource Misallocation: Without learning how cloud resources are used, companies may overestimate, leading to wasted resources and higher costs.
- Lack of Visibility: Lack of monitoring and reporting can lead to over budgeting which can make it difficult to manage expenses.
How to Avoid It
- Conduct a Detailed Cost Analysis: Before you migrate, you need to perform a cost-benefit analysis. You also need to consider the initial migration costs as well as long-term operational expenses. Also, integrate cloud cost calculators provided by top cloud providers.
- Adopt a Cloud Cost Management Tool: Integrate tools that will provide visibility to your cloud migration efforts. These tools can enable you to monitor resource usage, optimize costs as well as find areas where you can cut unnecessary expenses.
- Right-Size Your Resources: Work with the IT team to ensure only the necessary resources. This includes solutions such as auto-scaling, resource optimization strategies, etc.
- Regular Audits and Reviews: Determine the best method for auditing. To achieve this you need to determine the cloud spending as well as adjust various strategies to avoid budget overruns.
5. Insufficient Training and Change Management
The Pitfall
It’s worth noting that when implementing new technology and processes you need to adapt as well. Without the right training and change management teams can struggle to utilize the new systems effectively. This can lead to operational inefficiencies, reduced productivity, and frustration among employees.
Why It Happens
- Over-Reliance on Technology: Many organizations focus so much on the technical aspect of migration that they oversee the importance of educating the workforce to adapt.
- Resistance to Change: Employees accustomed to legacy systems may even resist new tools and processes.
- Inadequate Training Programs: If you skimp on training and support you can leave teams feeling unprepared and overwhelmed by the cloud environment.
How to Avoid It
- Develop a Comprehensive Training Plan: Invest in training programs that can cover both the technical and operational aspects of the new cloud environment. These training programs could include workshops, webinars, and hands-on training sessions.
- Communicate Benefits Clearly: Assist your team in understanding how the migration will make their work easier and more efficient. Stress upon improvements such as collaboration, scalability, and performance.
- Implement a Change Management Strategy: A strategic change management can assist you in a smooth transition. This involves clear communication, phased rollouts, and greater feedback and support.
- Provide Ongoing Support: You need to ensure that the support you provide is readily available during and even after the migration process. This also includes dedicated help desks, online resources, and regular check-ins to address concerns and gather feedback.
Prioritize training and change management, so that you can empower your employees to embrace the new cloud environment and also ensure that your migration activities are up to the specs.
Conclusion
Cloud migration can push businesses into a new era of agility, scalability, and innovation. But the path is riddled with various pitfalls such as inadequate planning and data complexities.
By understanding these common pitfalls and implementing the strategies outlined you can avoid costly mistakes and ensure a smooth and efficient migration.
With the right planning, continuous monitoring, and proactive management, your organization can avoid common pitfalls so that you can reap the benefits of modern organizations.